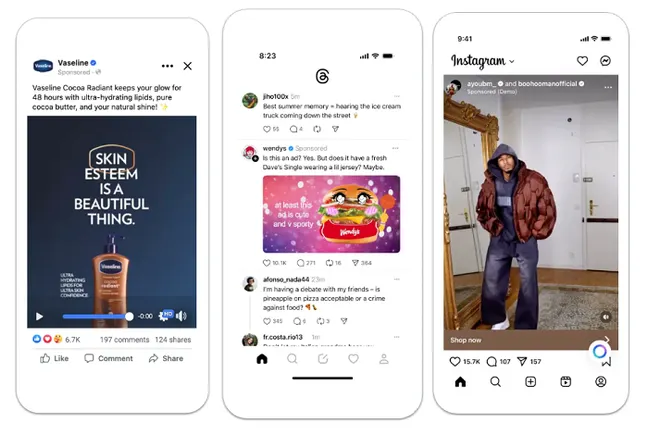
Phishing attacks that defeat MFA are easier than ever. So what are we to do?
Why multifactor authentication based on one-time-passwords and push notifications fail.

An entire cottage industry has formed around phishing attacks that bypass some of the most common forms of multifactor authentication (MFA) and allow even non-technical users to quickly create sites that defeat the protections against account takeovers.
MFA works by requiring an additional factor of authentication besides a password, for instance, a fingerprint, face scan, or the possession of a digital key. In theory, this prevents attackers from accessing an account even after they phish a victim’s username and password. Most often, the second form of authentication comes in the form of a one-time passcode that is sent to the user by text message or email or is generated by an authentication app that the user has already set up.
Adversary in the middle
As detailed on Thursday by Cisco Talos, an entire ecosystem has cropped up to help criminals defeat these forms of MFA. They employ an attack technique known as an adversary in the middle. The tools provide phishing-as-a-service toolkits that are marketed in online crime forums using names including Tycoon 2FA, Rockstar 2FA, Evilproxy, Greatness, and Mamba 2FA.




























































































































































_courtesy_VERTICAL.jpg)