This site uses cookies. By continuing to browse the site you are agreeing to our use of cookies.
All
YourStory.com
Inc.com
Fast Company
Entrepreneur
Startups – Crunchbase News
EU-Startups
Inc.com
Fast Company
Entrepreneur: Latest Articles
VentureBeat
How the Career Game Loop can help job seekers...
Apr 7, 2025 0
How the Career Game Loop can help job seekers...
Apr 7, 2025 0
A Minecraft Movie hits $301M global opening f...
Apr 7, 2025 0
A Minecraft Movie hits $110M global opening d...
Apr 6, 2025 0
All
GeekWireGeekWire
The Information
Mashable
Futurism
Techradar - All the latest technology news
Top News - MIT Technology Review
VentureBeat
The Register
The Hacker News
Digital Trends
CNET News.com
The Next Web
Gizmodo
Slashdot
TechCrunch
WIRED
The Verge - All Posts
Engadget
Ars Technica
Return Entertainment launches Rivals Arena sm...
Apr 7, 2025 0
From MIPS to exaflops in mere decades: Comput...
Apr 6, 2025 0
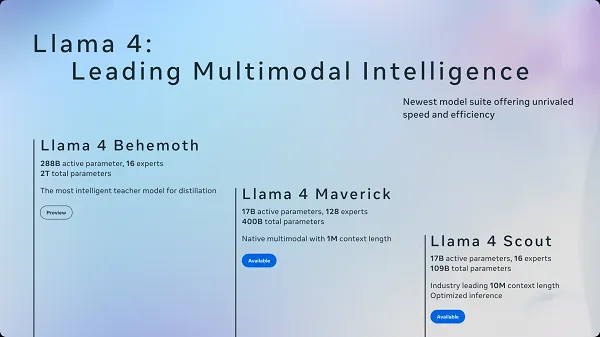
Meta’s answer to DeepSeek is here: Llama 4 la...
Apr 5, 2025 0
DeepSeek jolts AI industry: Why AI’s next lea...
Apr 5, 2025 0











![How to Find Low-Competition Keywords with Semrush [Super Easy]](https://static.semrush.com/blog/uploads/media/73/62/7362f16fb9e460b6d58ccc09b4a048b6/how-to-find-low-competition-keywords-sm.png)